Linux Security Howto
Means of securing your site 26. The kernel manages inputoutput requests from software memory processes peripherals and security among other hefty.
 Linux Security Howto The Linux Documentation Project
Linux Security Howto The Linux Documentation Project
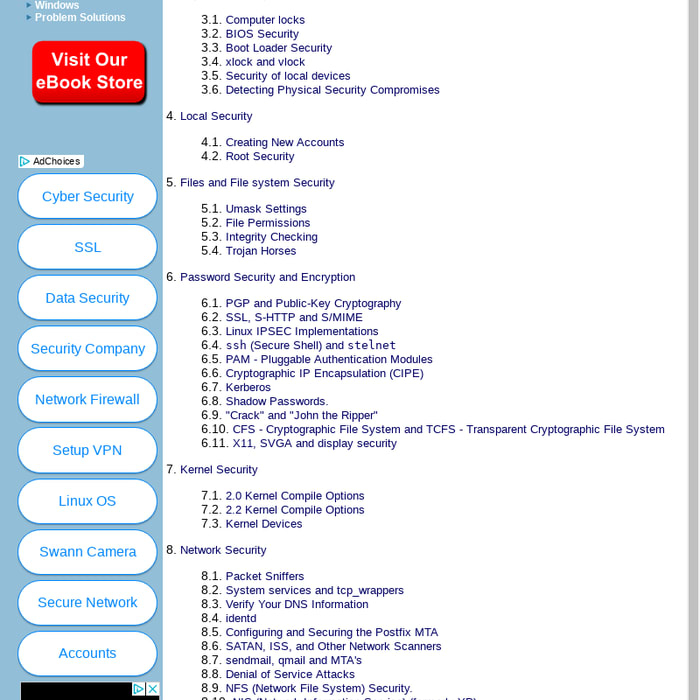
Introduction to linux security table of contents linux security for beginners.
Linux security howto. In this first part of a linux server security series i will provide 40 linux server hardening tips for default installation of linux system. Security of local devices 36. Introduction to linux security.
It covers general security philosophy and a number of specific examples of how to better secure your linux system from intruders. This document is a general overview of security issues that face the administrator of linux systems. Organization of this document 3.
Creating new accounts 42. Detecting physical security compromises 4. The linux kernel is the core component of the linux operating system maintaining complete control over everything in the system.
Xlock and vlock 35. This is also necessary if you want to install an older version of windows that wasnt developed with secure boot in mind such as windows 7. An os capable of effectively meeting the us governments security needs heading into 2020 date 16 dec 2019 linux kernel security in a nutshell.
It is the interface between applications and data processing at the hardware level connecting the system hardware to the application software. Boot loader security 34. S ecuring your linux server is important to protect your data intellectual property and time from the hands of crackers hackers.
It covers general security philosophy and a number of specific examples of how to better secure your linux system from intruders. We would like to show you a description here but the site wont allow us. How to secure your linux system.
Developing a security policy 25. Secure boot can be disabled which will exchange its security benefits for the ability to have your pc boot anything just as older pcs with the traditional bios do. The system administrator is responsible for security of the linux box.
 Linux Security Howto Kevin Fenzi 9780595136223 Amazon Com
Linux Security Howto Kevin Fenzi 9780595136223 Amazon Com
 How To Make Your Linux Server More Secure Linux Com
How To Make Your Linux Server More Secure Linux Com
 How To Secure A Linux Server 4 Steps With Pictures Wikihow
How To Secure A Linux Server 4 Steps With Pictures Wikihow
 How To Secure Linux Systems Auditing Hardening And Security
How To Secure Linux Systems Auditing Hardening And Security
 Linux Security Howto The Linux Documentation Project
Linux Security Howto The Linux Documentation Project
 How To Secure A Linux Server 4 Steps With Pictures Wikihow
How To Secure A Linux Server 4 Steps With Pictures Wikihow
 How To Secure A Linux Server 4 Steps With Pictures Wikihow
How To Secure A Linux Server 4 Steps With Pictures Wikihow
 How To Secure Your Linux System Techradar
How To Secure Your Linux System Techradar
 How To Configure Ssh Linux Security Tutorials
How To Configure Ssh Linux Security Tutorials
 The 10 Best Methods On How To Improve Linux Security
The 10 Best Methods On How To Improve Linux Security
.jpg?width=1500&name=Linux%20Security%20Simplified_%20How%20To%20Make%20Linux%20More%20Secure%20(With%20Less%20Work).jpg) Linux Security Simplified How To Make Linux More Secure
Linux Security Simplified How To Make Linux More Secure
 Linux Kernel Security And How To Improve It Linux Audit
Linux Kernel Security And How To Improve It Linux Audit
 Linuxsecurity How To Quickly Deploy A Honeypot With Kali
Linuxsecurity How To Quickly Deploy A Honeypot With Kali
 Exploring Kali Linux Alternatives How To Get Started With
Exploring Kali Linux Alternatives How To Get Started With
 Linux Kernel Security In A Nutshell How To Secure Your
Linux Kernel Security In A Nutshell How To Secure Your
 How To Use A Vpn To Improve Security On Linux Internet
How To Use A Vpn To Improve Security On Linux Internet
 How To Install The G Data Security Client For Linux Or Mac
How To Install The G Data Security Client For Linux Or Mac
 How To Delete Objects From The Kaspersky Security 8 0 For
How To Delete Objects From The Kaspersky Security 8 0 For
 Tutorial How To Write A Linux Security Module Casey Schaufler Intel
Tutorial How To Write A Linux Security Module Casey Schaufler Intel
How To Set Up An Sftp Server On Linux Guidebits
 How To Setup Linux In A Vm For Added Security Hide Me
How To Setup Linux In A Vm For Added Security Hide Me
 How To Manage Messages In The Backup Of Kaspersky Security
How To Manage Messages In The Backup Of Kaspersky Security
 How To Update Security Patches In Linux Using The Cli Nixcraft
How To Update Security Patches In Linux Using The Cli Nixcraft
 How To Secure Your Linux Server
How To Secure Your Linux Server
 Linux Security An Overview Notes From Linux Network Security
Linux Security An Overview Notes From Linux Network Security
 How To Secure Linux By Patching In Real Time Kernelcare
How To Secure Linux By Patching In Real Time Kernelcare
 How To Disable Selinux On Centos 7 Linuxize
How To Disable Selinux On Centos 7 Linuxize
 Download Computer Hacking Beginners Guide How To Hack
Download Computer Hacking Beginners Guide How To Hack
 Vps House Blog News Linux Technical Security Technical
Vps House Blog News Linux Technical Security Technical
 How To Disable Selinux On Centos 8
How To Disable Selinux On Centos 8
 Selinux Kubernetes Rbac And How To Ship Security Policies
Selinux Kubernetes Rbac And How To Ship Security Policies
 How To Run Imunifyav In Stand Alone Mode On A Linux Server
How To Run Imunifyav In Stand Alone Mode On A Linux Server
 How To Secure Your Internet Activity With Linux System And
How To Secure Your Internet Activity With Linux System And
 How To Update Linux Mint Real Linux User
How To Update Linux Mint Real Linux User
 How To Secure Lemp Stack Here Host Blog
How To Secure Lemp Stack Here Host Blog
 Amazon Com Computer Hacking Beginners Guide How To Hack
Amazon Com Computer Hacking Beginners Guide How To Hack
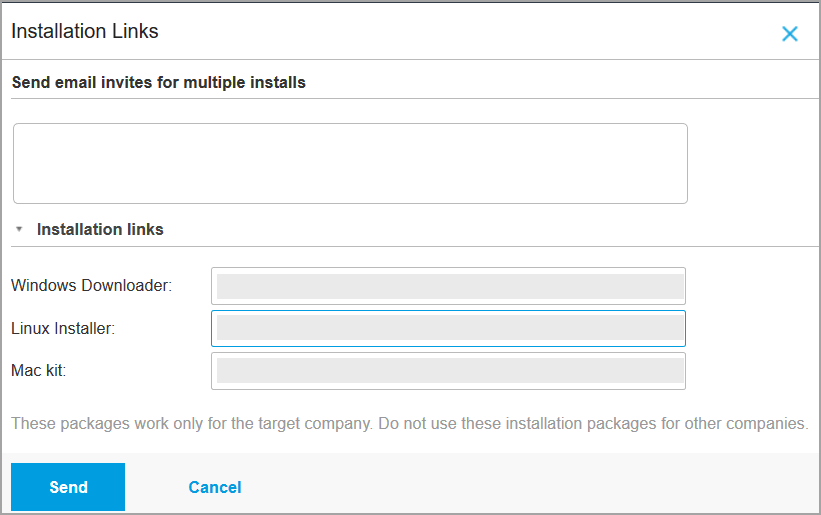 How To Install The Gravityzone Security Agent On Linux
How To Install The Gravityzone Security Agent On Linux
 How To Use Find Command On Linux 40 Examples Included
How To Use Find Command On Linux 40 Examples Included
 How To Secure Your Linux Cloud Server Secure My Webserver
How To Secure Your Linux Cloud Server Secure My Webserver
 How To Change The Default Ssh Port On Your Data Center Linux Servers
How To Change The Default Ssh Port On Your Data Center Linux Servers
 Linux How To Clone Website With Httrack Website Copier On
Linux How To Clone Website With Httrack Website Copier On
 Cara Boot Dan Instal Linux Di Uefi Pc Dengan Boot Aman
Cara Boot Dan Instal Linux Di Uefi Pc Dengan Boot Aman
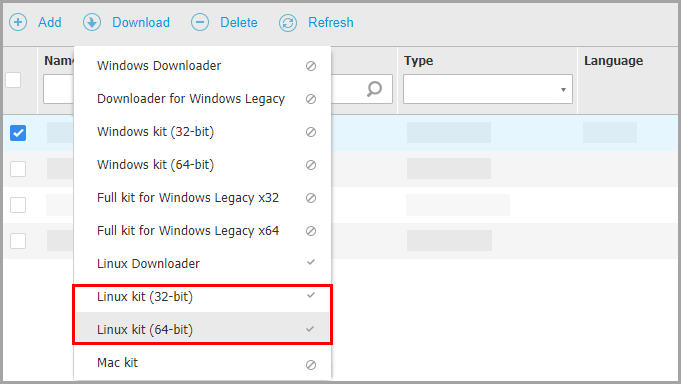 How To Install The Gravityzone Security Agent On Linux
How To Install The Gravityzone Security Agent On Linux
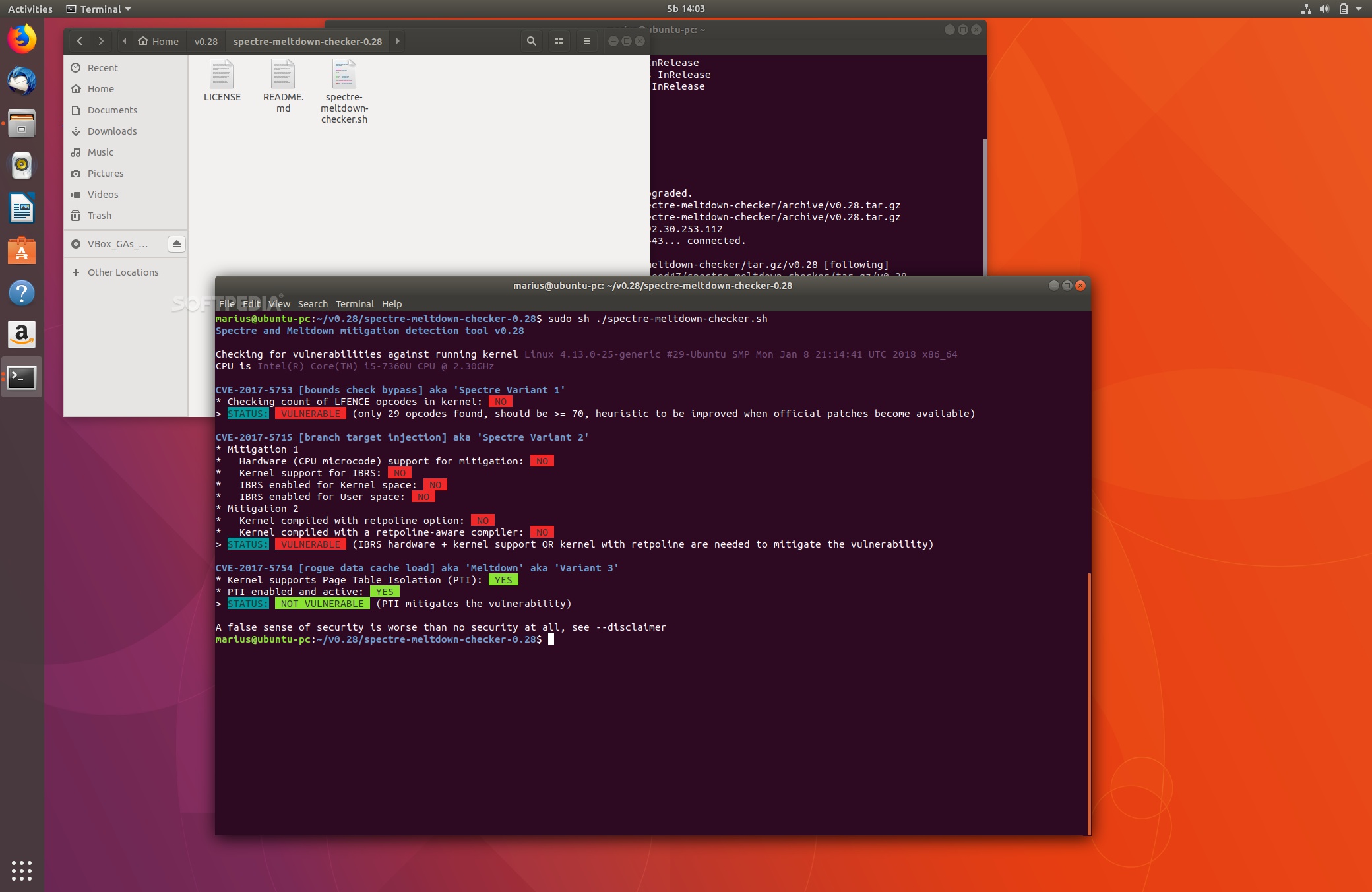
 How To Check If Your Linux Pc Is Vulnerable To Meltdown
How To Check If Your Linux Pc Is Vulnerable To Meltdown
 How To Secure Linux Home Server
How To Secure Linux Home Server
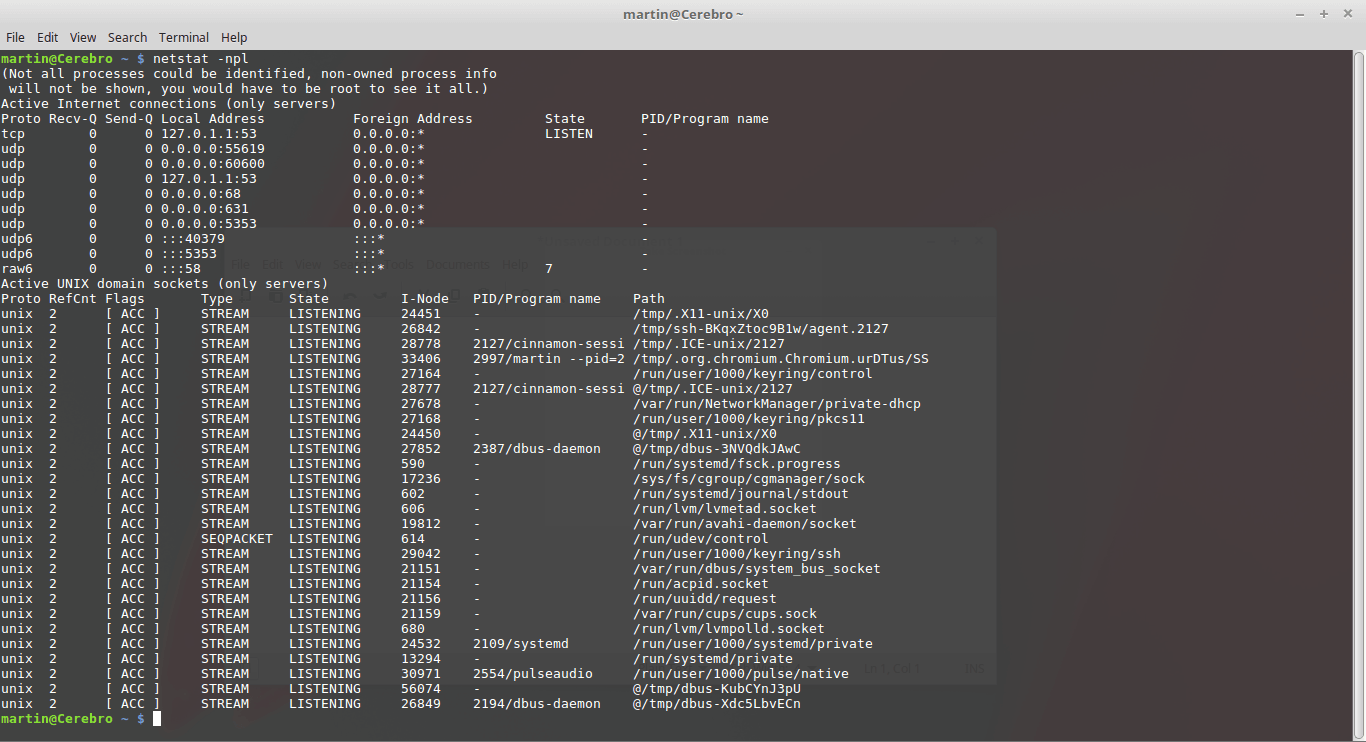 Top 15 Linux Security Questions You Didn T Know You Had
Top 15 Linux Security Questions You Didn T Know You Had
 Parrot Linux Os Terminal Commands List Tutorial Pdf
Parrot Linux Os Terminal Commands List Tutorial Pdf
 How To Configure Dvwa Damn Vulnerable Web Application In
How To Configure Dvwa Damn Vulnerable Web Application In
 How To Check If Your Linux Pc Is Vulnerable To Meltdown
How To Check If Your Linux Pc Is Vulnerable To Meltdown
 Secure Openssh Server Into Your Linux System Linux Concept
Secure Openssh Server Into Your Linux System Linux Concept
 Matthew Garrett Explains How To Increase Security At Boot
Matthew Garrett Explains How To Increase Security At Boot
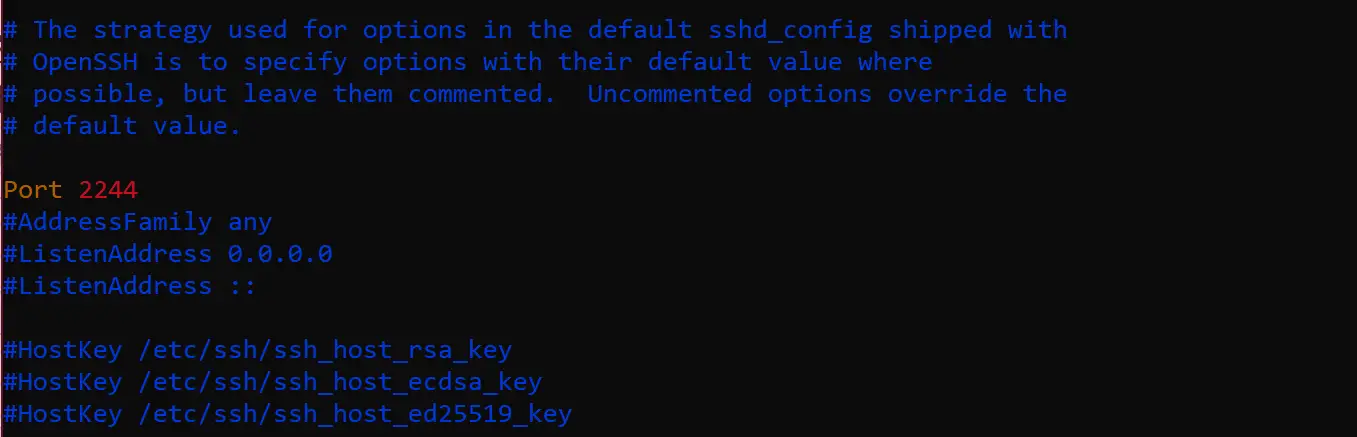 How To Configure Secure Ssh In Linux Infotech News
How To Configure Secure Ssh In Linux Infotech News
How To Enable Secure Shell Ssh On Ubuntu Linux Blackdown
 General Linux Information Mahir Yo Linux
General Linux Information Mahir Yo Linux
 Masternode Security Tutorial How To Install Basic Security On Your Linux Ubuntu Vps Masternode
Masternode Security Tutorial How To Install Basic Security On Your Linux Ubuntu Vps Masternode
 How To Verify Your Vpn Connection Is Secure Noobslab
How To Verify Your Vpn Connection Is Secure Noobslab
 How To Update Your Parrot Security Linux Distro To Newest
How To Update Your Parrot Security Linux Distro To Newest
 How To Configure A Kaspersky Security Center 9 0 Policy For
How To Configure A Kaspersky Security Center 9 0 Policy For
 Applying Patches How To Apply Patches In Linux Solarwinds Msp
Applying Patches How To Apply Patches In Linux Solarwinds Msp
 How To Install Update Linux Kernel 5 2 0 Rc7 On Ubuntu And
How To Install Update Linux Kernel 5 2 0 Rc7 On Ubuntu And
 Codingtrabla Tutorials Install Erp Cms Crm Lms Hrm On
Codingtrabla Tutorials Install Erp Cms Crm Lms Hrm On
 Linuxsecurity How To Quickly Deploy A Honeypot With Kali
Linuxsecurity How To Quickly Deploy A Honeypot With Kali
 How To Perform Comprehensive Linux Kernel Module Security
How To Perform Comprehensive Linux Kernel Module Security
 How To Tune Linux Permission For Maximum Security
How To Tune Linux Permission For Maximum Security
 How To Guide Basic Security Of Your Vpc Linux Academy
How To Guide Basic Security Of Your Vpc Linux Academy
 Linux Security Overview Ppt Video Online Download
Linux Security Overview Ppt Video Online Download
 How To Secure Your Linux Servers By Renato De Oliveira
How To Secure Your Linux Servers By Renato De Oliveira
 Top 25 Nginx Web Server Best Security Practices Nixcraft
Top 25 Nginx Web Server Best Security Practices Nixcraft
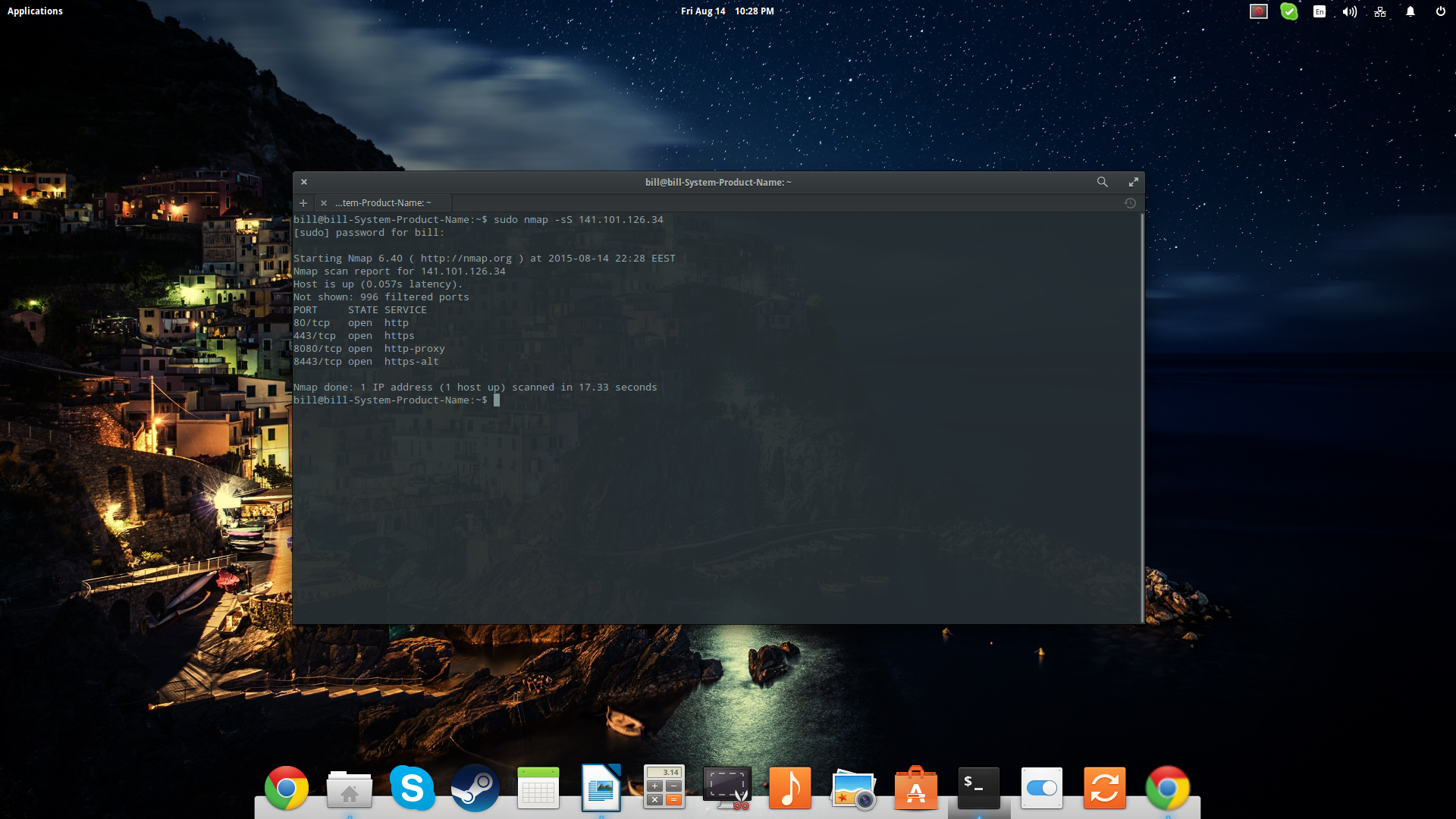 How To Use The Nmap Security Scanner On Linux
How To Use The Nmap Security Scanner On Linux
 Video How To Install And Setup Kali Linux Alpha Cyber
Video How To Install And Setup Kali Linux Alpha Cyber
 Howtoforge On Twitter How To Setup Automatic Security
Howtoforge On Twitter How To Setup Automatic Security
 20 Linux Server Hardening Security Tips Pdf Free Download
20 Linux Server Hardening Security Tips Pdf Free Download
 How To Install And Use Firejail On Linux
How To Install And Use Firejail On Linux
How To Check The Version Of Kali Linux
 How To Disable Ssh Password Login On Linux How To Disable
How To Disable Ssh Password Login On Linux How To Disable
 How To Secure Your Linux Web Server
How To Secure Your Linux Web Server
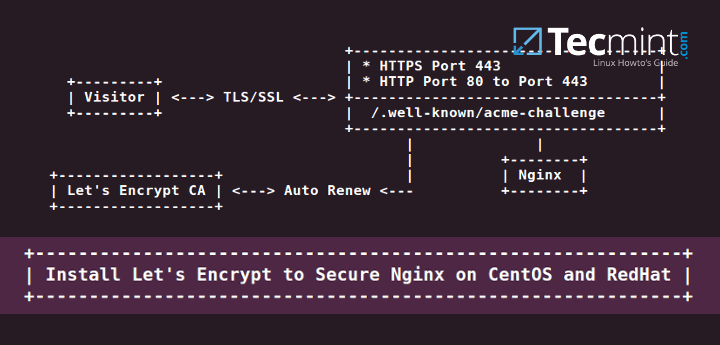 How To Secure Nginx With Let S Encrypt On Centos 8
How To Secure Nginx With Let S Encrypt On Centos 8
 How To Protect Linux Users With Mcafee Endpoint Security
How To Protect Linux Users With Mcafee Endpoint Security
 Tuto Security Browser Here S How To Properly Operate The
Tuto Security Browser Here S How To Properly Operate The
 How To Keep Debian Linux Patched With Latest Security
How To Keep Debian Linux Patched With Latest Security
 How To Setup A Local Dns Caching Server On Linux
How To Setup A Local Dns Caching Server On Linux
 How To Install Setup Apache Tomcat Server On Linux Ubuntu
How To Install Setup Apache Tomcat Server On Linux Ubuntu
 How To Check Apparmor Status Unix Tutorial
How To Check Apparmor Status Unix Tutorial
 How To Install And Use A Vulnerability Scanner In Linux
How To Install And Use A Vulnerability Scanner In Linux
 Truecrypt Smartcards And Security Tokens Howto Prerequisites
Truecrypt Smartcards And Security Tokens Howto Prerequisites
How To Use Network Security Toolkit Nst In Linux
 How To Secure A Linux Server And How To Run It Smoothly
How To Secure A Linux Server And How To Run It Smoothly
 How To Conigure Raid Over Lvm In Redhat Linux Ccna Windows
How To Conigure Raid Over Lvm In Redhat Linux Ccna Windows
 Project Paper How To Use Linux Operating Systems As A
Project Paper How To Use Linux Operating Systems As A
 Kernel 5 3 Stable Release How To Upgrade On Ubuntu System
Kernel 5 3 Stable Release How To Upgrade On Ubuntu System
 How To Install And Get Started With Kali Linux Iot Tech Trends
How To Install And Get Started With Kali Linux Iot Tech Trends
 How To Setup Secure Private Peer To Peer Continuous File
How To Setup Secure Private Peer To Peer Continuous File
 How To Open Bitlocker Drive On Linux Using Dislocker
How To Open Bitlocker Drive On Linux Using Dislocker
 How To Check Security Updates List Perform Linux Patch
How To Check Security Updates List Perform Linux Patch
 Hackontuesday Episode 7 How To Install Docker On Kali Linux
Hackontuesday Episode 7 How To Install Docker On Kali Linux
 How To Install Snort Ids On A Linux System
How To Install Snort Ids On A Linux System